We had taken on a new client and we were excited to get started enhancing services for their employees. During our initial orientation we noticed a few items that caught our attention and we created a 5-step process to get them to “best in class” status.
We began with the items that needed attention first and we were pleased how the day was going. It was time in the project to log onto their computers and perform some testing when we noticed something strange.
The email server rebooted after updates and refused to come back on. While beginning to assess that situation we logged into the finance server, and that’s when it all came crashing down.

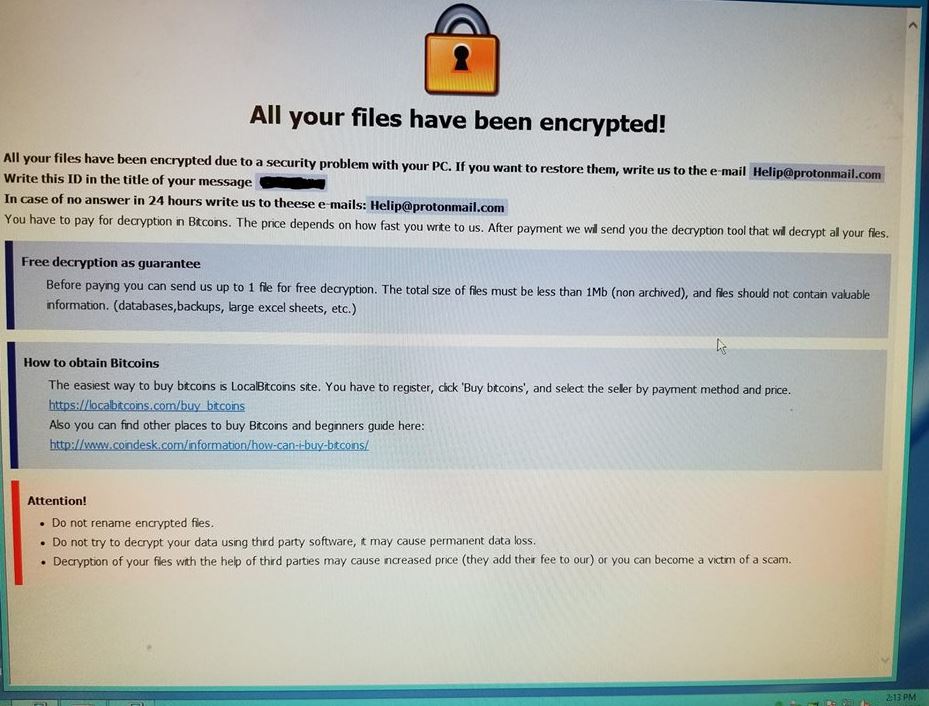
Apparently, just nine hours before we were to start this new chapter for our client, they were hit with ransomware.
When a computer is hit with ransomware a ransom note is displayed on the victim’s computer after an attack and is unique to each victim. The message displays a code with instructions on how to send money anonymously to the attacker. A couple of servers and a handful of workstations had been infected in the attack, each with their own ransom note.
The makers of the “SamSam”, a threat that appeared in 2015, have collected almost $6 million since its release. 74% of the known victims are based in the United States while other attacks have been reported including Canada, the UK, and the Middle East. The security software and hardware company Sophos reported a ransom paid by one individual victim to be $64,000.
This attack used a new version of the crypto virus “Dharma”, a member of the CrySiS ransomware family.
It had left a .combo file extension at the end the majority of the files on the computer. This means that after Dharma encrypts files it leaves the files no longer able to be opened and appends the file name with .id-{victimID}.[e-mail].combo to each encrypted file.
Not only were their documents, images, and other data affected, but also the OS configurations and data files required to run applications (e.g., Microsoft Office).
The three IT security organizations that are noted to be familiar with Dharma are Kaspersky, Emsisoft and Trend Micro. Since we are Trend Micro partners, we reached out to their support team. We were surprised to find that the reason that the attack went undetected was that this was a new variant of Dharma that the support team had not seen. It was a busy week and we’ve worked with them to identify this new strain and they will add it to their list of threats.
If not for cloud-based back-up and restoration options, it could have been much worse.
Oh, and remember our initial orientation when we noticed a few items that caught our attention? One item was their backup strategy. During our initial inspection, we setup their servers to back their data up to the cloud, allowing us to restore their data to a server quickly so that they could access and resume working.
So why is this important to you and your co-workers? The infection process of Dharma ransomware is conducted primarily via spammed e-mails that use a deceptive message to get people to click open them. They often pretend to be sent from PayPal, USPS, or FedEx and often contain links or attachments that pretend to be invoices or other important communication.
So make sure you talk about this at the water cooler, so you can raise awareness in your workplace about this massive industry that is raking in the cash from many small and medium businesses.
.
We at Advanced Systems Solutions have helped many organizations protect their data from harm. If you’re looking for a support company to help keep you safe, with unmatched customer service, please contact us. We love to help!
.
Like our Facebook page by clicking on the icon at the top right of this page to stay up to date with current alerts and information!
Disclaimer: The above information is not intended as technical advice. Additional facts or future developments may affect subjects contained herein. Seek the advice of an IT Professional before acting or relying on any information in this communiqué.